The Complete Cyber Security Course : Anonymous Browsing!

Why take this course?
🌐 The Complete Cyber Security Course: Anonymous Browsing! 🚀 Volume 3: Become a Cyber Security Specialist, Master Anonymity, Hide my IP, Tor, Privacy, Proxy Servers, and Best VPN 🔒
Learn a practical skill-set in staying anonymous online and maintaining total privacy against even a well-resourced adversary with global influence. This course is your comprehensive guide to mastering the art of cyber security privacy on all major platforms, including Windows, MacOS, Linux, iOS, and Android, as well as specialized environments like Tails, Whonix, and more.
Become a cyber security specialist. This easy-to-follow advanced course will take you from beginner to expert in the world of cyber security privacy. You'll gain knowledge that is critical for maintaining your digital footprint minimal and your activities secure.
We cover in detail all the best anonymizing and privacy methods:
- Tor: The Onion Router, a free and open-source software for enabling anonymous communication.
- VPNs (Virtual Private Networks): Secure tunnels across the internet to protect your privacy.
- Proxy servers: HTTP, HTTPS, SOCKs, and Web proxies.
- SSH Secure Shell: A protocol for securely gaining remote access over insecure networks.
- Live Operating Systems: Tails, Knoppix, Puppy Linux, Jondo live, and Tiny Core Linux.
- OPSEC (Operation Security): The process of ensuring that your actions and information cannot be traced or exposed.
- I2P (The Invisible Internet Project): A network where communication is denied by design to the external observer.
- JonDoNym: An anonymizing proxy, a VPN for privacy protection.
- Off-site connections: Securely connecting from hotspots and cafes.
- Mobile, Cell Phones & Cellular Networks: Staying anonymous while on the move.
- Bulletproof hosting: Understanding the infrastructure that supports services that are otherwise typically shut down by mainstream providers.
For each of these anonymizing methods, we analyze their strengths and weaknesses, discuss the techniques used to attack these systems, and provide you with strategies to mitigate those de-anonymization attacks.
Advanced anonymity: We explore chaining and nesting different anonymizing services together to create a robust privacy framework that stands up against the most sophisticated adversaries.
We also cover how to bypass censors, firewalls, and proxies, including techniques for evading deep packet inspection (DPI). Learn how to navigate the internet freely from anywhere in the world.
This course covers both the theory and practically of setting up everything we discuss. You'll walk away with hands-on experience that will prepare you for real-world scenarios.
This is volume 3 of 4 of your complete guide to cyber security privacy and anonymity. By the end of this series, you'll be equipped with a comprehensive skill set that makes you a formidable expert in the realm of digital privacy. Whether you're looking to protect sensitive data, ensure secure communications, or simply enhance your personal privacy online, this course will empower you to take control of your digital life and defend it against any intrusion. Join us on this journey to master the art of staying anonymous online. 🔑✨
Enroll now and embark on your journey to becoming a Cyber Security Specialist with The Complete Cyber Security Course: Anonymous Browsing! Volume 3 awaits you. Let's dive deep into the world of cyber security, privacy, and anonymity. 💻🔎
Course Gallery

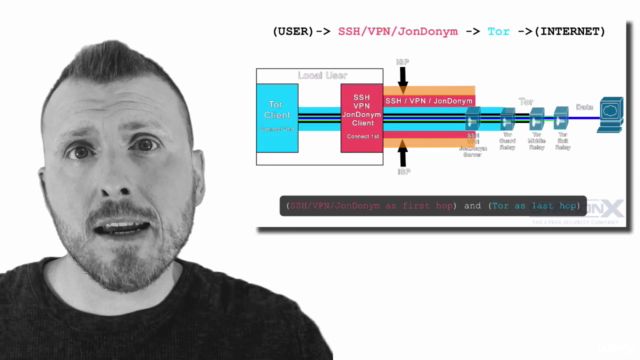
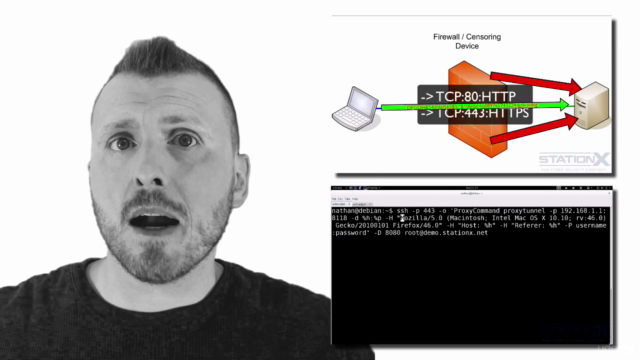
Loading charts...
Comidoc Review
Our Verdict
The Complete Cyber Security Course: Anonymous Browsing offers a comprehensive look at various cybersecurity concepts. Despite some outdated sections, it remains a valuable resource for those looking to gain practical experience with cybersecurity tools and techniques. However, be prepared to do additional research and find alternative resources that cover newer technologies.
What We Liked
- In-depth coverage of a wide range of cybersecurity topics, making it a comprehensive resource for those new to the field
- Practical exercises that provide hands-on experience with tools and techniques commonly used in the industry
- Excellent course quality, with clear presentations and valuable information that covers many areas of security and anonymity
- High-quality content that teaches you how to think about cybersecurity and find solutions by yourself
Potential Drawbacks
- Some sections are outdated, which can be frustrating for learners and may require additional research to stay current
- Resource links in the course material may point to removed or deprecated content, making it difficult to access some resources
- Lectures on anonymity may feel irrelevant to some learners who are not concerned about nation-state adversaries
- Limited coverage of certain topics and newer technologies, such as ChromeOS and RAM-based VPN servers