Security in Spring Boot REST Web Service Applications

Why take this course?
🚀 Course Title: Security in Spring Boot REST Web Service Applications
🎓 Headline: Master the Art of Securing Your Spring Boot Applications with Spring Security, JWT, SSL/TLS, HTTPS, and Public Key Infrastructure (PKI)!
🔒 Course Description:
Embark on a comprehensive practical journey through the world of secure Spring Boot REST web service applications. This course is designed to guide you step-by-step, leveraging the robust Spring Security framework to implement authentication, authorization, and encryption.
Core Topics Include:
- Filters and Configuration: Understand the intricacies of securing your application with Spring Security's filters and customizable configuration settings. 🛡️
- Authentication: Learn how to authenticate users in a secure manner, ensuring that only authorized individuals can access your system. 🔐
- JSON Web Tokens (JWT): Master the use of JWTs for maintaining user authentication state across HTTP requests. 📜
- Role-based Authorization: Implement fine-grained access control based on user roles and permissions within your application. 🗝️
- Cybersecurity Principles: Gain insights into the general principles and concepts that form the backbone of secure software design. 🛡️
- Cryptography: Dive deep into encryption, encoding, and hashing techniques to protect sensitive data. 🔑
- Symmetric and Asymmetric Encryption: Understand the differences and uses between symmetric and asymmetric encryption in securing your application's communication. 🔫
- HTTP over SSL/TLS (HTTPS): Secure all communication with HTTPS to ensure data integrity and confidentiality during transmission. ⤵️
- Digital Certificates & Public Key Infrastructure (PKI): Establish a secure environment by implementing digital certificates and PKI for mutual authentication and encryption. 🏫
- TLS Cipher Suites and Handshakes: Learn the technicalities behind SSL/TLS handshake procedures and cipher suites to ensure secure connections. 🤝
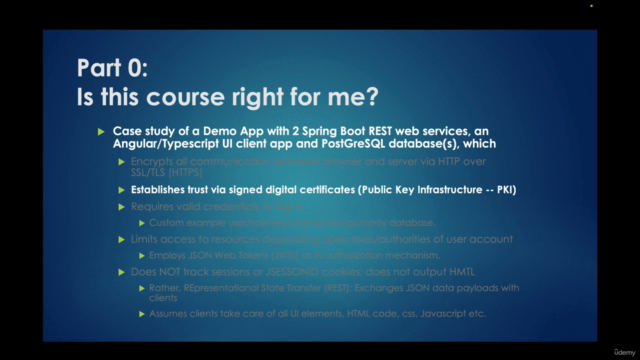
🛠️ Real-world Case Study: A Demo App Walkthrough
This course includes a detailed case study of a demo application that utilizes Spring Boot REST web services, an Angular/Typescript UI client app, and a PostGreSQL database(s). The application will demonstrate practical implementations of the concepts learned.
Key aspects of the case study include:
- HTTPS Communication: Ensures all data exchanged between the browser and server is encrypted. 🔒
- Digital Certificate Trust: Implements signed digital certificates for mutual trust assurance through PKI. 🌐
- User Authentication: Requires valid credentials for user login, with a custom example user/role/resource/action/authority database. 🔗
- Role-based Access Control (RBAC): Demonstrates the development of authorization mechanisms based on user roles and authorities. 🎫
- JSON Web Tokens (JWTs): Shows how JWTs can be employed for authentication in a stateless manner. 📱
- No Session Tracking: The application does not rely on session tracking or JSESSIONID cookies, outputting only JSON data payloads. 🛑
- RESTful Approach: Emphasizes the exchange of data between clients using REST principles over HTML forms or other presentation technologies. 🚀
⚫️ Course Structure Breakdown:
This course is structured to guide you from the basics to the advanced topics in a logical and progressively challenging manner. Here's what you can expect:
- Part 0: Is this Course Right for Me? An introductory section to assess if this course aligns with your learning goals and current skill level. 🤔
- Part 1: General Cybersecurity Principles. A foundational segment covering the essential principles and concepts of cybersecurity that underpin secure application design. 🏗️
- Part 2: Introducing the Demo App and its Components. A detailed overview of the demo application's architecture, components, and objectives. 📝
- Part 3: Application Security Before Spring Security. An exploration of security considerations before integrating Spring Security into your application. 🔍
- Part 4: The Spring Security Framework in Our Demo App. Practical implementation of Spring Security within the demo application, step by step. 🛠️
- Part 5: A Deeper Dive into Spring Security Architecture and Theory. Advanced concepts and theoretical underpinnings that will solidify your understanding and application of Spring Security. 🧠
Join us on this journey to secure your Spring Boot REST web service applications with the latest in cybersecurity best practices! 🌟
Course Gallery



Loading charts...