Securing IoT: From Security to Practical Pentesting on IoT

Why take this course?
🌐 Securing IoT: From Security to Practical Pentesting on IoT
🚀 Course Description:
The Internet of Things (IoT) has expanded the horizons of connectivity, but with this expansion comes a host of security challenges. This course is your key to understanding and securing IoT systems, culminating in practical penetration testing using industry-specific tools. 🔒
Dive into IoT Systems:
Start by dissecting the components and technologies that make up IoT systems. You'll explore various IoT use cases across industries such as connected vehicles, microgrids, and enterprise drone systems. Understand the threats, attack vectors, and security regulations that govern IoT systems. Learn about common security architectures and Privacy by Design (PbD) principles, including a walk-through of a Privacy Impact Assessment (PIA).
Master IoT Security Fundamentals:
In the first part of this course, Fundamentals of IoT Security, you'll cover:
- Use Cases Across Various Industries: Gain insights into how IoT is used in different sectors and the unique security challenges each presents.
- IoT Components and Technologies: Get a grasp of the hardware, RTOS, APIs, messaging protocols, and backend services that underpin IoT systems.
- Security Regulations and Standards: Stay compliant with current security regulations and standards applicable to IoT systems.
- Common Security Architectures: Learn about the various architectures designed to protect IoT systems.
- Threat Identification and Mitigation: Recognize potential threats and the necessary mitigations to secure your IoT systems effectively.
Hands-On Pentesting:
In the second part, Hands-On IoT Penetration Testing, you'll:
- Device Architecture Understanding: Gain insights into the common vulnerabilities found in IoT devices, including networks and hardware.
- Practical Pentesting: Learn to perform penetration testing on a range of advanced IoT devices, such as Amazon Echo, Logitech Cameras, Google Nexus phones, Vyos Gateways, TP-Link Smart Switches, and firewalls.
- Create Detailed Pentesting Reports: Develop the skills to document your findings effectively after completing a pentest.
Who are the Experts Behind This Course?
This course is crafted by industry experts:
-
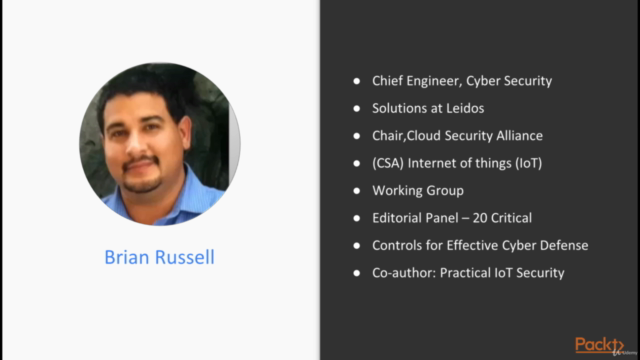
Brian Russell is a chief engineer specializing in cybersecurity solutions for IoT at Leidos. He leads teams in designing security solutions and implementing privacy and trust controls, with a focus on IoT devices like UAS and connected vehicles. Brian has 16 years of experience in information security and plays a key role as the chair of the Cloud Security Alliance (CSA) Internet of Things (IoT) Working Group and as a member of the FCC's Technological Advisory Council (TAC) Cybersecurity Working Group, supporting initiatives like the Center for Internet Security (CIS) 20 Critical Security Controls Editorial Panel.
-
Sunil Gupta is a certified ethical hacker with extensive experience in teaching cybersecurity online to over 45,000 students across 150+ countries. His expertise lies in vulnerability assessment, penetration testing, intrusion detection, risk identification, data analysis, reporting, and briefing.
Join this course to equip yourself with the knowledge and skills required to secure IoT systems and perform effective pentests, paving your way to becoming an IoT security expert. 🛡️✨
Course Gallery


Loading charts...