Web security: Injection Attacks with Java & Spring Boot

Why take this course?
🎓 Web Security: Master Injection Attacks with Java & Spring Boot
🚀 Course Headline: Ethical Hacking, Web Application & Spring Security - Conquer NoSQL, LDAP, LOG, CSV & SQL Injection!
Course Description:
Are you a Java web developer aiming to master secure coding practices? Or perhaps you're intrigued by the world of Ethical hacking and Web application security? 🛡️ Whether you fit into either category or are just looking to enhance your cybersecurity knowledge, this hands-on course on Injection Attacks is tailored for you!
In collaboration with OWASP (Open Web Application Security Project), this course focuses on one of the top vulnerabilities from the OWASP Top 10 list - injection attacks. Injection attacks remain a dominant threat in the cyber world, and understanding them is crucial for developing secure web applications.
Key Highlights:
- Up-to-date Content: The course leverages the latest versions of Spring Boot and other dependencies, with regular updates provided by the instructor. 🛠️
- Captions Available: For an enhanced learning experience, subtitles are included in the videos to help you follow along more easily. 📽️
Learn from a Pro:
Ali Gelen, with practical knowledge as part of both blue and red security teams, is here to guide you through injection vulnerabilities in detail. 🎓✨
Course Focus:
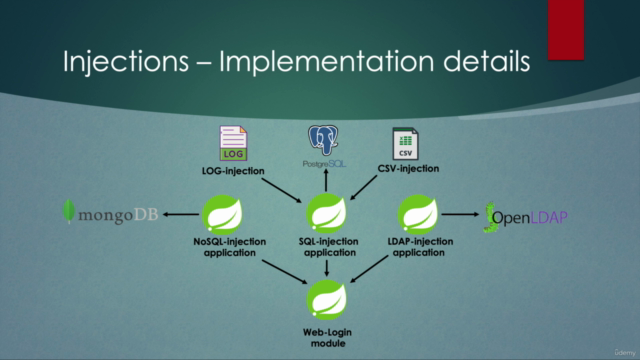
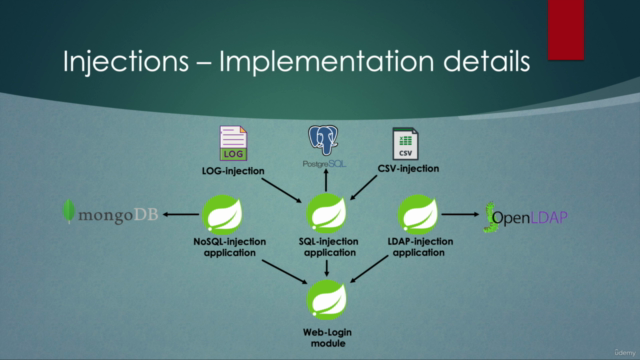
You'll delve into various types of injection attacks, including:
- SQL Injection
- NoSQL Injection
- LDAP Injection
- LOG Injection
- CSV Injection
By understanding these attack vectors, you'll gain a deeper insight into the security concepts and be well-prepared to protect web applications effectively. 🛡️
Hands-on Approach:
- Develop Vulnerable Applications: Learn by doing by creating common web login modules with Thymeleaf and Bootstrap, and implement Spring Security for form-based authentication and authorization.
- Hacking & Exploitation: Explore how to exploit applications using different injection attack techniques and Ethical hacking examples.
- Protection Strategies: Discover the defense-in-depth principle, applying multiple solutions to each vulnerability to secure your web application in layers. 🔐
Technologies & Data Sources:
- Java & Spring Boot: The core technologies for building robust applications.
- Spring Security: For form-based authentication and authorization.
- Data Sources: Practical experience with PostgreSQL for SQL Injection, MongoDB for NoSQL injection, and OpenLDAP for LDAP injection.
Course Structure:
Each section includes:
- Development of Vulnerable Applications (or jump straight into hacking by using provided source codes)
- Injection Techniques & Exploitation
- Security Measures & Best Practices
Additional Insights:
- Source Code Downloads: Get the source code for SQL, NoSQL, LDAP, LOG, and CSV injections from lectures 20, 38, 51, 60, and 74 respectively. Ensure to install the necessary data sources as detailed in the lectures.
- Broken Access Control Suggestion: A valuable suggestion from a student, Manoj Singh, to include topics on "Broken Access Control" has been noted!
Enrollment Benefits:
- Full Money-Back Guarantee: A 30-day guarantee to enroll with confidence and join this learning adventure risk-free! 💰🚫
Don't miss out on the opportunity to elevate your skills in web security and Ethical hacking. Enroll now and take control of your cybersecurity journey with Java & Spring Boot! 🚀🌐
Testimonials:
- "Talented instructor and great course!!! Just a small suggestion, If you could add a chapter about 'Broken Access Control' topic that will be a great help." - Manoj Singh
Join the ranks of informed and skilled security professionals today! 🛡️🚀
Course Gallery


Loading charts...