Complete Real-World Ethical Hacking 2022

Why take this course?
🛡️ Complete Real-World Ethical Hacking 2022 🚀
Course Headline:
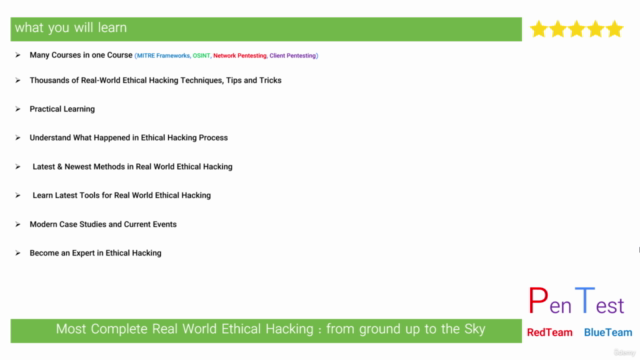
🎓 Learn and review many modern courses just in one course as fast as possible!
Course Description:
Welcome to this comprehensive Ethical Hacking course that will take you deep into the world of cybersecurity! This course is meticulously designed for those who have prior knowledge of networking. It's a practical journey that will allow you to exploit various elements such as Network Infrastructure Devices (Switch & Router) and Client (Windows 10), ensuring you don't waste time on theoretical lectures that don't stick.
Course Structure: 📚
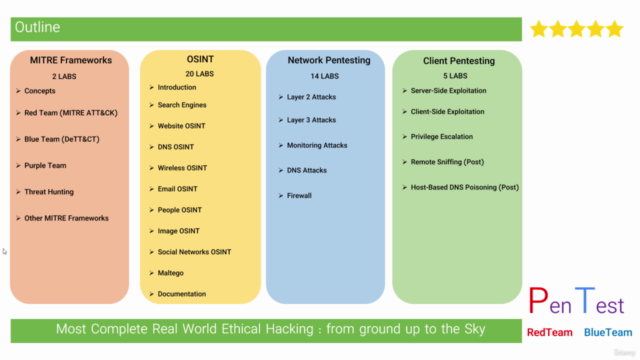
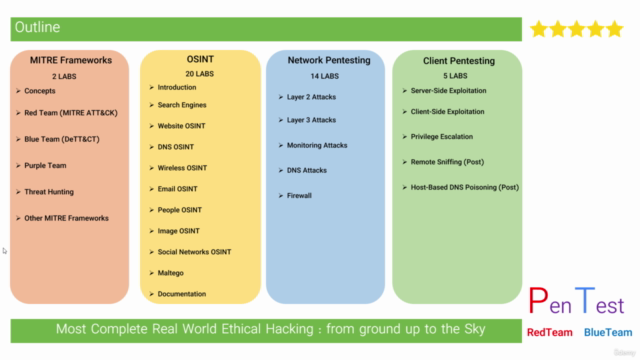
Section 1: MITRE Frameworks
Dive into the world of MITRE Frameworks with a focus on practical applications and understanding. You'll explore:
- MITRE ATT&CK Framework: Discover how it operates, its real-world use, and how to leverage the MITRE ATT&CK Navigator.
- DETT&CT Framework for Blue Teams and Investigators: Understand its application and utility.
- Threat Hunting Methodology (TaHiTI): Get to grips with how it works and introduce yourself to the MaGMa Use Case Framework.
- MITRE Cyber Analytics Repository (CAR), MITRE D3FEND, MITRE ENGENUITY, MITRE Engage, and MITRE RE&CT Frameworks.
Section 2: Open-source intelligence (OSINT)
Ideal for Ethical Hackers, Investigators, and Researchers, this section covers a wide array of OSINT techniques and tools, including:
- Mastering Search Engines, Dark Web Forums, and Spiderfoot for Website Analysis.
- Exploring DNS Records and Analysis Tools, Wireless OSINT, Email OSINT, People OSINT, Image OSINT with OCR Technology, and Social Networks like Twitter and Facebook.
- Learning Maltego from basics to advanced techniques, including Footprint Machine Levels and documentation.
Section 3: Network Penetration Testing
This section teaches you how to identify and exploit vulnerabilities at various network layers, such as:
- Layer 2 Attacks, like CDP/LLDP Recon, CAM Table Overflow, ARP Spoofing, Vlan Hopping, and Spanning-Tree Protocol (STP) attacks.
- Layer 3 Attacks, including Cisco Password Decryption, DHCP Starvation, FHRP Protocol attacks.
- Monitoring Attacks like Log Spoofing and Log DDoS.
- DNS Attacks such as DNS Spoofing and DNS Amplification.
- Firewall Pentesting Steps to secure your network.
Section 4: Client Penetration Testing
Learn to exploit client systems effectively through Metasploit Framework, including:
- Server-Side Exploitation and Client-Side Exploitation using Metasploit.
- Privilege Escalation techniques that bypass User Access Control (UAC).
- Post-Exploitation attacks like Remote Sniffing and Host-Based DNS Poisoning.
Educational Note: 📝
This course is designed for educational purposes only, and all techniques are practiced in a lab environment set up by Hamed Mehdi. It's important to note that this course is not affiliated with any other organization or a certification exam. Upon completion, you will receive a Course Completion Certification from Udemy, signifying your expertise in Ethical Hacking.
Embark on this journey to become an Ethical Hacking expert and secure your digital world! 🛡️✨
Course Gallery

Loading charts...