Hacking Wireless Networks. Theory and practice.

Why take this course?
Course Title: 🌟 Hacking Wireless Networks. Theory and Practice 📡
Course Headline: 🚨 38% of secured Wi-Fi networks are vulnerable to the attack which can be carried out by a 12-year-old in 4 minutes! HOW?
LAST UPDATED: 11/2023
Welcome to Hacking School!
Before we begin our journey into the world of wireless network hacking, let's clarify one thing: the practical use of this course has been proven by thousands of individuals across the globe - from beginners to seasoned cybersecurity professionals. Whether you aim to fortify your home WiFi network, retrieve a forgotten password, or delve into the security of your wireless network to verify its resilience, this course offers valuable insights and techniques.
Ethical Wireless Network Hacking Course Overview:
This course is designed to cover all the crucial techniques related to WIRELESS NETWORK (or WiFi) HACKING. It's an indispensable guide for hackers, system administrators, penetration testers, and cybersecurity enthusiasts alike. In today's era where wireless networks are omnipresent, understanding their security is essential. As encryption standards evolve, so do the methods of exploitation. This is an ongoing arms race, and this course keeps you ahead of the curve.
What You Can Expect:
- Comprehensive Lectures: Access to over 60 lectures on Wireless Network Hacking.
- Detailed Handbook: A downloadable, over 180-page course handbook in PDF format.
- Training Operating System v2.0 CE: A fully equipped OS tailored for your hacking activities, including CUDA support.
- Legal and Safe Practice: All techniques demonstrated must be used ethically within a controlled environment.
- Money-Back Guarantee: 30 days to explore the course. Your satisfaction is guaranteed or your money back!
Video Training Sessions:
- Configuring Wireless Network Card Modes
- Changing the MAC address of the wireless network card
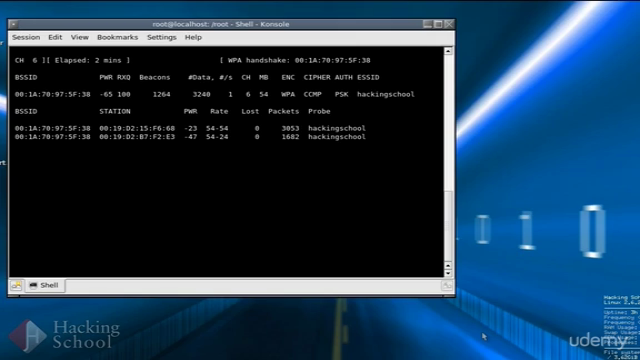
- Finding a hidden access point with disabled ESSID broadcast
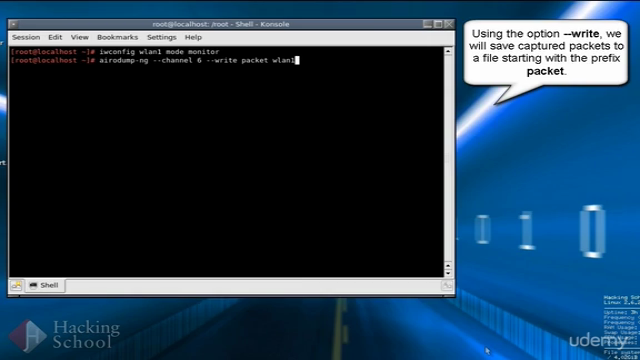
- Utilizing deauthentication attacks for traffic jamming
- Overview and demonstration of the chop-chop attack
- Generating packets without knowing the network key
- Interactive packet replay and ARP request replay
- Demonstration of the PTW (Patient Traffic Watcher) and KoreK attacks
- Creating a fake access point - The Caffe Latte attack
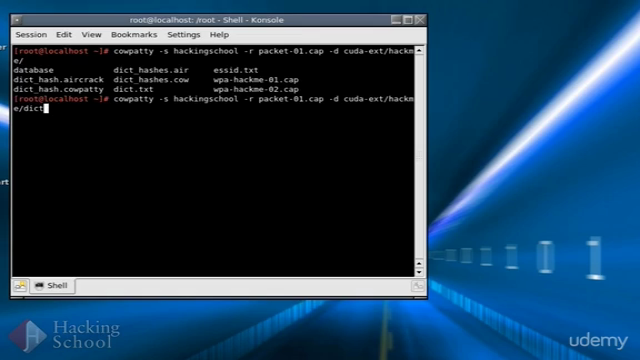
- Dictionary attacks on WPA/WPA2
- Optimization of dictionary attacks using hash tables
- Setting up CUDA for the environment
- Installing CUDA-SDK and CUDA-Toolkit
- Compiling and installing tools with CUDA support
- Generating your own dictionary
- Cracking MD4 and MD5 hashes with CUDA technology applications
Your Learning Path:
- Understanding the Basics: Learn about the fundamental aspects of wireless networks, including their modes and configurations.
- MAC Spoofing: Discover how to change your MAC address, a common technique used in network security assessments.
- Stealthy Networking: Find out how to detect hidden access points and understand the importance of ESSID broadcasts.
- Disruption Techniques: Explore deauthentication attacks, which can disrupt network connections as part of your research or testing.
- Chop-Chop Attack: Understand this attack method that allows an attacker to inject management frames into a wireless network.
- Packet Crafting: Learn how to generate packets without needing the network key, a crucial step in many penetration tests.
- ARP Poisoning and Replay: Gain hands-on experience with packet replay attacks, which can lead to man-in-the-middle scenarios.
- WPA/WPA2 Attacks: Dive into the methods of cracking WPA and WPA2 encrypted networks, including dictionary attacks and CUDA optimizations.
- CUDA for WiFi Security: Utilize CUDA technology to speed up hash computations and network security testing.
Your Ethical Responsibility:
It is imperative to understand that the techniques presented in this course must be used responsibly, within a controlled environment. This course provides all the necessary tools and information to prepare your own training system. Please refer to the Legal information in the 1st section for further guidance on ethical practices.
Satisfaction Guaranteed:
We are confident that you will find this course enlightening and beneficial. We offer a full refund within 30 days if you're not completely satisfied with your purchase, no questions asked.
Good luck, and we look forward to guiding you through the complex and intriguing world of wireless network security!
Trainer: Andrew Harper || Hacking School Team
Your Cybersecurity Adventure Awaits!
Course Gallery
Loading charts...