Ethical Hacking: Vulnerability Research

Why take this course?
🌐 Course Title: Ethical Hacking: Vulnerability Research
🚀 Headline: Find and Run Exploits! 🚀
👤 Instructor: Peter Acourse
Unlock the World of Cybersecurity with Ethical Hacking!
Are you curious about the dark arts of cybersecurity? Have you ever wondered how hackers exploit vulnerabilities to compromise systems? If so, this course is your gateway into the fascinating and critical field of ethical hacking.
Course Overview:
-
Understanding Vulnerabilities and Exploits: You'll learn what vulnerabilities are and how they can be exploited to gain unauthorized access or cause harm to systems.
-
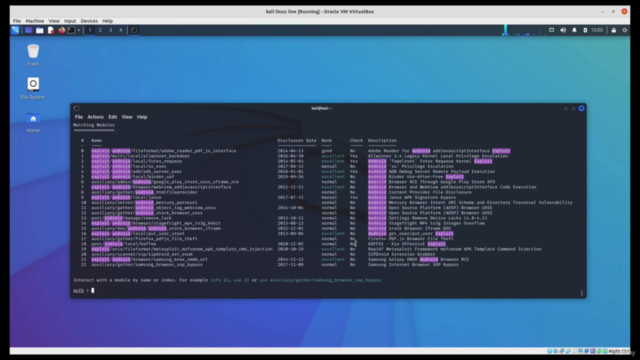
Identifying Software Vulnerabilities: Discover the tools and techniques used to identify outdated or vulnerable software on a system.
-
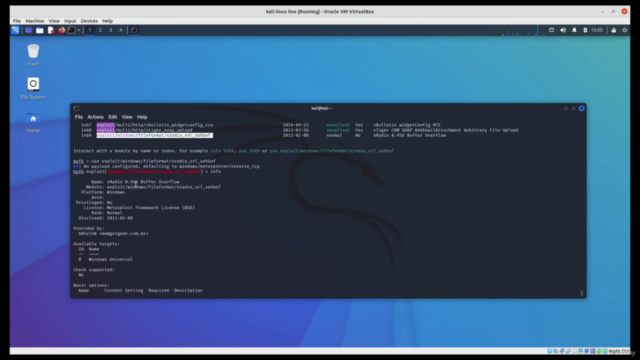
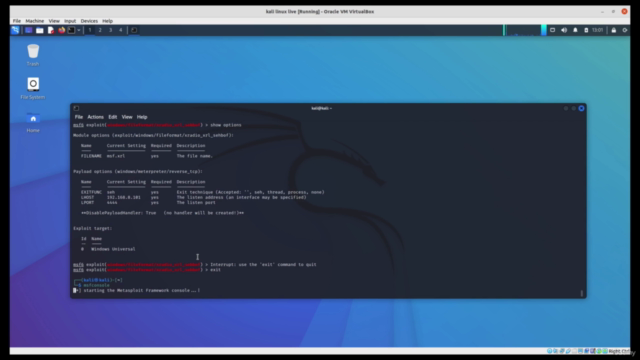
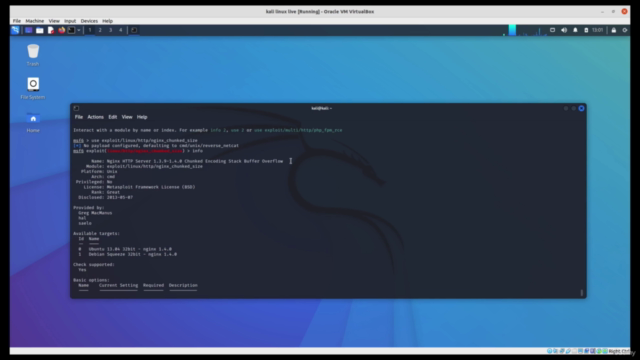
Running Exploits: Gain practical experience in finding and running exploits, including hands-on exercises with both Ubuntu 16.04 and Windows 2000 environments using Virtual Box.
Why Take This Course?
✅ Practical Skills: By the end of this course, you'll know how to:
- Describe what vulnerabilities are and where to find them.
- Configure and run exploits using Metasploit, a powerful framework for exploiting vulnerabilities.
✅ Hands-On Learning: This isn't just theory—you'll work with real systems and software to understand the practical aspects of ethical hacking.
✅ Career Foundation: Whether you're starting a career in cybersecurity or simply curious about hacking, this course will provide you with a solid foundation of knowledge and skills.
What You'll Need:
- A basic understanding of operating systems (Windows, Linux).
- Access to Kali Linux, which can be downloaded for free or acquired as a Kali Live USB.
- Virtual Box installed on your computer to create separate environments for practicing hacking techniques.
Course Structure:
-
Introduction to Ethical Hacking: Understanding the basics and ethical considerations of hacking.
-
Vulnerability Research: Learning how to find vulnerabilities in software and systems.
-
Exploit Development with Metasploit: Mastering the use of Metasploit for configuring and running exploits.
-
Practical Exercises: Hands-on experience with real-world scenarios on both Ubuntu 16.04 and Windows 2000 systems.
-
Final Project: By the end of the course, you'll complete a capstone project where you'll exploit vulnerabilities in both an Ubuntu 16.04 and a Windows 2000 system, demonstrating your newfound skills.
Who Is This Course For?
This beginner-level course is designed for:
- Aspiring cybersecurity professionals.
- Individuals with an interest in ethical hacking and how to protect systems from attacks.
- Those looking to expand their knowledge of computer security and risk management.
Enroll now to embark on your journey into the world of ethical hacking and vulnerability research. With "Ethical Hacking: Vulnerability Research," you'll gain the knowledge and skills necessary to make a difference in cybersecurity. 🛡️💻
Course Gallery
Loading charts...